Google and Samsung will release new security updates for Android phones every month, in an attempt to prevent the platform from falling behind in the fight against malware.
The two companies’ announcements come in the wake of an embarrassing bug in Android’s media handling framework, called Stagefright, which had been dubbed “Heartbleed for mobile” after the desktop virus of that name. Despite being warned about Stagefright in April, the vast majority of Android phones were weak to the vulnerability when security researcher Joshua Drake went public with it 90 days later.
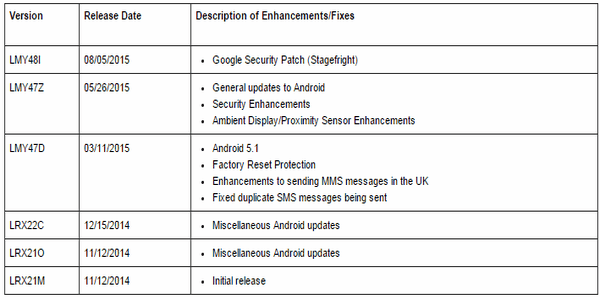
Google’s Android Stagefright patch is flawed. (aka Google Stagefright ‘tx3g’ MP4 Atom Integer Overflow) was quite simple, consisting of merely 4 lines of changed code,” Jordan. Learn more about when Google plans to patch the recent Stagefright vulnerability that was detected a few days ago, and which could silently cause trouble. Google has just released LMY48I OTA update based on Android 5.1.1 Lollipop for all Nexus devices. Among minor bug fixes and other performance improvements, the update comes with a patch for a serious security issue on Android devices called Stagefright. Stagefright Detector is designed to keep you informed about the status of your device. Stagefright Detector will not fix the vulnerability, because the vulnerability can only be fixed once a patch is released by Google, your carrier or your device manufacturer, which typically is delivered through a System Update.
Alongside the new frequent security updates, Google has finally released a patch for Stagefright for its own Nexus line of phones, which it sells directly to customers. The company argues that the majority of users weren’t at risk, however, with application sandboxing limiting the amount of damage an attacker could do.
Adrian Ludwig, lead engineer for Android Security, said: “From this week on, Nexus devices will receive regular OTA updates each month focused on security, in addition to the usual platform updates … Nexus devices will continue to receive major updates for at least two years and security patches for the longer of three years from initial availability or 18 months from last sale of the device, via the Google Store.”
Samsung partially matched Google’s offering, confirming that users of the company’s mobile phones would receive their own security updates once a month. Dong Jin Koh, Samsung’s head of mobile research, said: “With the recent security issues, we have been rethinking the approach to getting security updates to our devices in a more timely manner. Since software is constantly exploited in new ways, developing a fast response process to deliver security patches to our devices is critical to keep them protected.
“We believe that this new process will vastly improve the security of our devices, and will aim to provide the best mobile experience possible for our users.” Samsung has not, however, matched Google’s promise to patch devices for at least three years from release.
The Android platform has been regularly criticised for the time it takes for it to get critical security updates to users. Google, which runs the Android Open Source Project, the coding initiative at the heart of the operating system, does not have direct relationships with the vast majority of Android users. Instead, it fixes the open-source part of Android, before passing the fixes on to device manufacturers such as Samsung.
Frequently, those manufacturers themselves then have to check with the mobile phone carriers before they are able to push out updates to the devices. Given the low profit margins on many Android phones, support dries up quickly.
In July, security reporter Lorenzo Franceschi-Bicchierai wrote that these problems had led him to ditch the platform entirely for Apple’s iPhone.
He wrote: “This is the fundamental difference between Android and iPhone. When there’s a bug on iOS, Apple patches it and can push an update to all iPhone users as soon as it’s ready, no questions asked.
“When the same thing happens with Android, Google patches and then … God knows when the AT&Ts, Verizons, HTCs, and Sonys of the world will decide it’s important enough that they should care and send you the update with the patch (though, to their credit, they’re starting to care, mostly because having an updated OS is now seen as a competitive advantage). Hell, even Google-owned Nexus phones, which the company has full control over, haven’t been patched for Stagefright yet.”
Following Google’s announcement, the most popular Android are, or will be, fixed this month. The company confirmed fixes for the HTC One M7, One M8, One M9, LG Electronics G2, G3, G4 and Sony Xperia Z2, Xperia Z3, Xperia Z4, and Xperia Z3 Compact.
In tandem with the release of Android Marshmallow 6.0 for Nexus phones, Google has also delivered a critical security update for Nexus devices vulnerable to the latest Stagefright bugs.
Revealed last Friday, Stagefright 2.0, like its predecessor, has left virtually every Android device in the wild exposed to a dangerous attack on the operating system's media player engine, which can be triggered after receiving a malicious MP3 or MP4 media file.
Joshua Drake, of mobile security firm Zimperium, reported the new Stagefright bugs to Google in mid-August and the Android Security Team has released fixes for the issues in its October monthly security update.
Google said it notified Open Handset Alliance partners about Stagefright 2.0 on September 10 or earlier and would release source-code patches for these issues to the Android Open Source Project (AOSP) repository.
The Stagefright 2.0 bugs fixed in this update affected libutils in all versions of Android from Lollipop 5.1.1 down to Android 1.0, while another fixed flaw affected the same libstagefright component that was exploited by Stagefright 1.0. The second flaw was limited to Android 5.0 and higher.
Android has long ruled the consumer smartphone market – but can it make an impact on the business market too?
Google Stagefright Patch Download
The update contains a total of five critical fixes covering more than a dozen individual flaws, as well as five high-severity privilege escalation issues affecting libFLAC, KeyStore, Media Player Framework, Android Run time, Mediaserver, and Secure Element Evaluation Kit. There are also several more moderate and low severity fixes in the update.
Google had already addressed a weakness that made Stagefright dangerous by updating Hangouts and Messenger applications to not automatically pass media to vulnerable processes like mediaserver.

Even since Stagefright's disclosure, the Android maker has maintained that the OS's address space layout randomisation (ASLR) would have thwarted actual attacks on devices. However, last month its own security researchers at Project Zero revealed this security feature could in fact be bypassed.
Nonetheless, the severity of Stagefright spooked Google into committing to monthly security updates for its Nexus 4, 5, 6, 7 and 9 devices, which began in August.
Samsung and LG vowed to follow suit with monthly security updates of their own. But president of HTC America, Jason Mackenzie, has cast doubt on the viability of those commitments, noting on the weekend that it would be 'unrealistic' for any vendor to guarantee monthly security updates when patches are often held back by carrier testing.
'Sometimes you won't receive due to lack of space in their labs. They only handle so many projects at once,' Mackenzie explained to a developer on Twitter.
Carrier across the globe were quick to deliver Stagefright fixes soon after the bug was revealed, yet despite the promise of monthly updates, carrier-certified versions of LG, Samsung, and HTC devices are still waiting to receive Stagefright fixes.
According to support pages of Australian carrier Telstra, the Stagefright fix for HTC's One M8 has been retracted due to an issue with the over-the-air firmware package, while updates for Samsung's Galaxy S5 has been approved but are still waiting to be deployed.
Patches for LG's G4 were 'deploying' in late September. Dozens of other mid-range and flagship devices have not received fixes yet either.
Google's Nexus devices are another matter, and device owners should be getting an over-the-air update in the next few days. Alternatively, they can get the builds from Google's developer site.
'Builds LMY48T or later - such as LMY48W - and Android M with Security Patch Level of October 1, 2015 or later address these issues,' Google notes in the bulletin.
Given the update delays to carrier-certified Android devices, if Stagefright comes under a serious attack, it could make rooting a handset and installing CyanogenMod a more secure option.
Latest Wow Patch Download
Cyanogen developers announced yesterday that Google's security release had hit AOSP code and has now been merged in CM 12.1 source. CM 12.1 nightly builds for over 50 devices now already contain Google's October security fixes, the developers noted.
Read more about Android



